Gurucul XDR Uses Machine Learning & Integration for Real-Time Threat Detection, Incident Response
To improve speed and intelligence of threat detection and response, Gurucul’s cloud-native XDR platform is adding machine learning, integration risk scoring and more.
The latest upgrade to the Gurucul XDR platform adds “extended detection and response” alongside improved risk scoring to strengthen security operations effectiveness and productivity.
Improvements to Gurucul’s cloud-native solution also sport features to enable intelligent investigations and risk-based response automation. New features include extended data linking, additions to its out-of-the-box integrations, contextual machine learning (ML) analytics and risk-prioritized alerting.
The driving force behind these updates is to provide users a “single pane of risk,” according to Gurucul CEO Saryu Nayyar.
“Most XDR products are based on legacy platforms limited to siloed telemetry and threat detection, which makes it difficult to provide unified security operations capabilities,” Nayyar said.
Gurucul Cloud-native XDR is vendor-agnostic and natively built on a Big Data architecture designed to process, contextually link, analyze, detect, and risk score using data at massive scale. It also uses contextual Machine Learning models alongside a risk scoring engine to provide real-time threat detection, prioritize risk-based alerts and support automated response, Nayyar.added.
Gurucul Real-Time XDR Automation
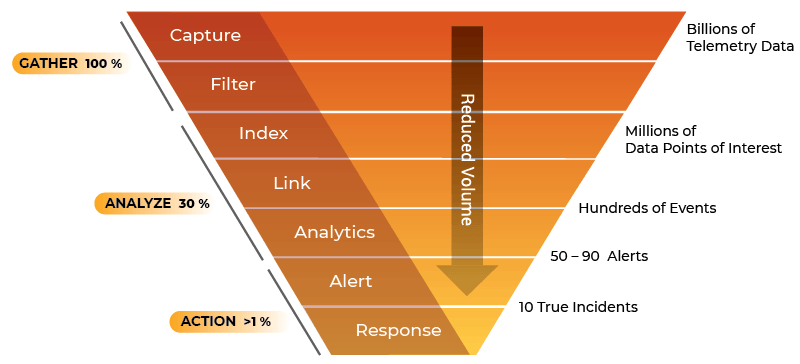
Gurucul XDR provides the following capabilities that are proven to improve incident response times:
AI/ML Suggestive Investigation and Automated Intelligent Responses: Traditional threat hunting tools and SIEMs focus on a limited number of use cases since they rely on data and alerts from a narrow set of resources. With cloud adoption increasing at a record pace, threat hunting must span hybrid on-premises and cloud environments and ingest data from vulnerability management, IoT, medical, firewall, network devices and more.
Gurucul’s approach provides agentless, out-of-the-box integrations that support a comprehensive set of threat hunting applications. These include: Insider threat detection, Data exfiltration, Phishing, Endpoint forensics, Malicious processes and Network threat analytics.
Incident Timeline, Visualizations, and Reporting: Automated Incident Timelines create a smart link of the entire attack lifecycle for pre-and post-incident analysis. Timelines can span days and even years of data in easy-to-understand visualizations.
Gurucul’s visualization and dashboarding enables analysts to view threats from different perspectives using several widgets, including TreeMap, Bubble Chart, etc., that provide full drill-down capabilities into events without leaving the interface. The unique scorecard widget generates a spider chart representation of cyber threat hunting outcomes such as impact, sustaining mitigation measures, process improvements scores, etc.
Risk Prioritized Automated Response: Integration with Gurucul SOAR enables analysts to invoke more than 50 actions and 100 playbooks upon detection of a threat to minimize damages.
Entity Based Threat Hunting: Perform contextual threat hunting or forensics on entities. Automate and contain any malicious or potential threat from a single interface.
Red Team Data Tagging: Teams can leverage “red team” exercise data and include supervised learning techniques as part of a continuous AI-based threat hunting process.
Analyst Firm Gartner Takes Note of Gurucul’s Integration Approach
According to Gartner, “XDR products aim to solve the primary challenges with SIEM products, such as effective detection of and response to targeted attacks, including native support for behavior analysis, threat intelligence, behavior profiling and analytics.”
Further, “the primary value propositions of an XDR product are to improve security operations productivity and enhance detection and response capabilities by including more security components into a unified whole that offers multiple streams of telemetry,” Gartner added.
The result, the firm said, is to present options for “multiple forms of detection and . . multiple methods of response.”
Gurucul XDR provides the following capabilities that are proven to improve incident response times by nearly 70%:
Surgical Response
- Automate response actions with risk-based triggers and orchestration playbooks
- Customize machine learning models to automate responses based on specific triggers
- Automate workflows to execute the right response and mitigate threats
- Based on newly discovered threat patterns, use pre-built threat categorizations to prioritize threat hunting
Intelligent Centralized Investigation
- Based on unified risk score, prioritize users and entities for investigation
- Visualize the entire kill chain to investigate incidents
- Accelerate investigations using big data to mine linked users, accounts, entitlements, structured and unstructured data, along with risk score and peer group analytics
- Search across any combination of structured and unstructured data for a 360 view of user and entity behavior
- Unify telemetry logs for contextual searches on big data for root-cause analysis after-the-fact and reduce investigation time
Rapid Incident Correlation and Causation
- Contain threats across multiple layers faster with detailed correlation and contextual data
- Leverage automated incident timelines that create smart links of the entire attack lifecycle for pre-and post-incident analysis
- Effectively trace attack origin and reconstruct steps with intelligent risk-prioritized telemetry data
- Use AI to uncover behavior patterns and data relationships that map to search profile
Gurucul XDR is available immediately from Gurucul and its business partners worldwide.






