Ping Intelligent Identity Platform Adds Integrations, Guides To Ease Delivery of Zero Trust Security
Ping Identity is adding support for Zero Trust security with new capabilities, practical guidance, and technology integrations. Further, IDN looks at Ping’s latest offering combines the worlds of identity and intelligence
Ping Identity has rolled out a Zero Trust security infrastructure with new capabilities, practical guidance, and technology integrations.
The Ping Intelligent Identity Platform is architected as a comprehensive, standards-based platform that allows users and devices to securely access any service, application or API from any device. Optimized for hybrid IT environments, The Ping Intelligent Identity Platform can be deployed on-premises, in the cloud, or both, and provides centralized control to maximize the balance of security and convenience for all primary use cases.
According to Ping executives, as organizations move away from a static perimeter-based security approach, there is a need to embrace a new approach that requires authentication and authorization of every user, device, and network.
Enter Zero Trust, and where Ping notes its importance:
Adopting a Zero Trust security strategy allows you to open your applications and data to anyone, anywhere, with minimal friction and maximum connectivity. This helps today’s mobile users consume resources hosted in private datacenters and public clouds from corporate and personal devices. It also enhances security.
In action, Ping’s latest offering combines the worlds of identity and intelligence. As a result, Ping Intelligent Identity Platform is designed to provide organizations what Ping calls “an advanced degree in identity intelligence” with a range of capabilities to support passwordless authentication, real-time and risk-aware authorization, and other features.
Under the covers, Ping brings a range of capabilities, including:
- Artificial intelligence to analyze and detect anomalous behavior
- Integration with multiple risk, fraud and threat signals
- Policies to enforce authentication/authorization business rules
- Multiple authentication methods to obtain varying levels of assurance
- Ability to sync, aggregate and secure information from multiple sources
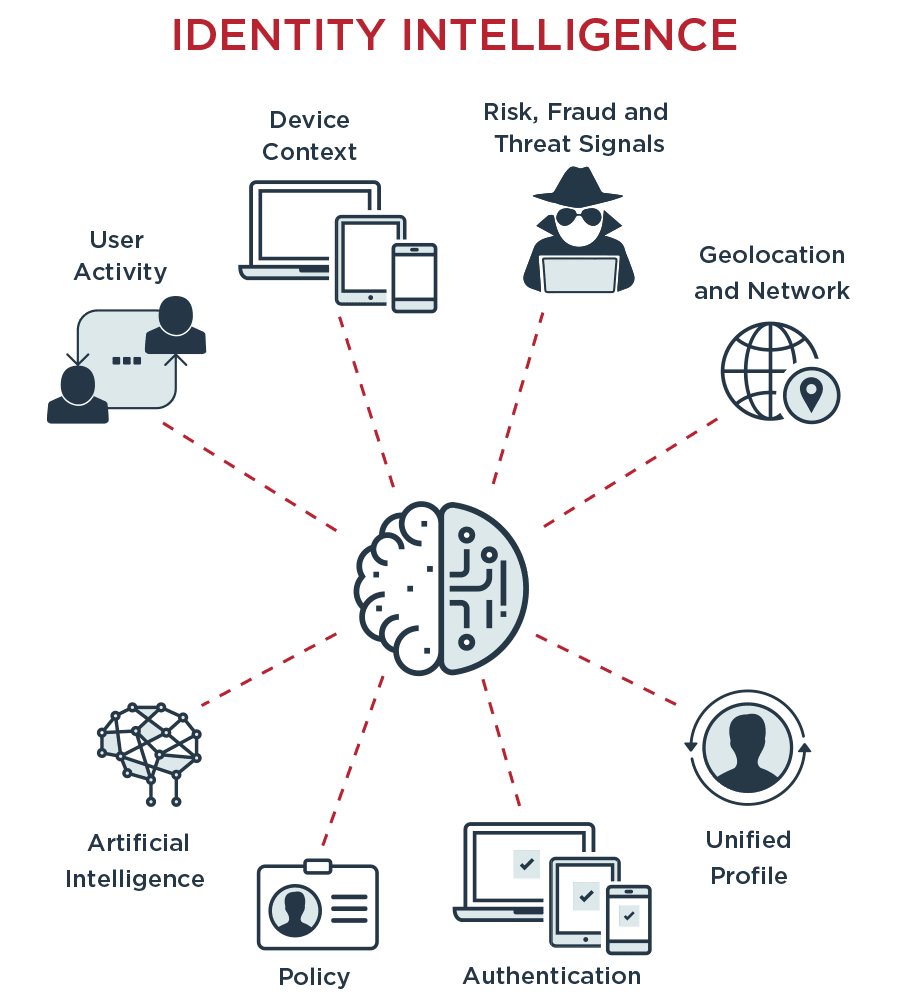
Among some notable outcomes from Ping’s marriage of “identity’ and “intelligence” is the ability to improve both security and user experience – rather than have to trade off one for another.
Among some examples are:
Manage Identities: The Ping Intelligent Identity Platform is architected for enterprise hybrid IT environments. Further, it provides several options to align your identity and access management (IAM) solution with an organization’s resources, customization needs and preferred deployment model.
Extensible and Customizable: Because organizations can differ widely in their requirements, Ping uses open standards for maximum interoperability and extensibility. It also provides extensive APIs for integration and customization.
Self-Service: Because managing identities and customer experiences at enterprise scale is challenging, Ping looks to offer several self-service features for admins, developers and even end users. Administrators can control product and environment configurations from a top-level IAM admin (or via a delegated business application admin view in PingCentral, a converged platform operating portal). Developers can quickly embed identity services into their apps. Admins can also safely give end users a full suite of self-service tools to let them secure manage their own registration, account updates and resets, data sharing consent and more.
Enterprise-wide Global Authentication. Users can leverage the Ping Intelligent Identity Platform as a central authentication authority for all workforce, partner and customer use cases. The platform lets users orchestrate a wide range of authentication use cases with policy-based controls over who has access to user-related data to address data privacy challenges.
Ping Partners Share Views on the Latest Feature Rollout
More benefits arise thanks to integration with several Ping partners – ID DataWeb, MobileIron and Zscaler.
“ID DataWeb and Ping Identity partner to verify that users are who they say they are during device registration as part of step-up authentication and account recovery. Continuous identity verification is an essential security component,” said ID DataWeb vice president of product and operations Matt Cochran in a statement.
“MobileIron and Ping Identity together offer greater context for device posture assessment and corresponding policy creation to allow or deny user access,” noted Brian Foster, MobileIron’s senior vice president of product management. “Ping Identity provides an authentication authority, which, when combined with our unified endpoint management software allows for heightened security based on a range of device attributes.”
Zscaler senior vice president of business and corporate development, Punit Minocha, said, “Traditional security methods that treat users as an IP address and rely on firewall appliances hosted in a datacenter are antiquated in today’s mobile cloud-driven workplace. We are happy to be working with Ping Identity to help protect enterprise data and enable cloud transformation by bringing together two Zero Trust ecosystem leaders built with user experience and scalability in mind.”







